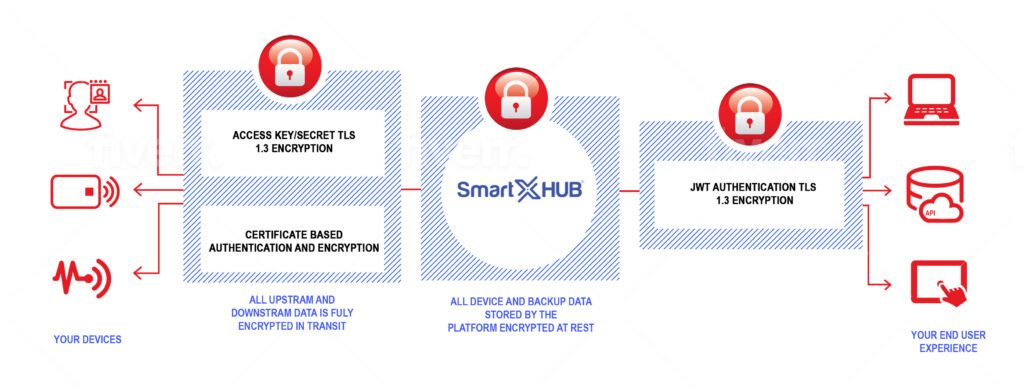
Transport Security
All communication between devices and SmartX HUB is fully encrypted using the Transport Security Layer (TLS). TLS is an industry-standard encryption scheme and most commonly used by browsers to encrypt HTTPS data. TLS is widely adopted and available on most embedded devices, languages, and operating systems.
API Security Tokens
API access is controlled by the industry-standard JSON Web Tokens authentication mechanism. Users create remote API access tokens through the account dashboard. The types of resources available to the token can be individually controlled by the Company depending on the needs of the specific API client. API access tokens can be revoked at any time.
It is up to the user to securely save this information. You cannot recover a token if it is re-generated. The scope of each token is securely encrypted directly into the token, which is decrypted by Smartx HUB server-side.
Infrastructure Security
Smartx HUB uses Google Compute as its underlying infrastructure provider. All data is stored using Google Compute Engine’s persistent disk functionality, which encrypts all data in transit and at rest. Google complies with the strictest information and physical security requirements. Please refer to their security documentation for more information.
DDoS Attack Protection
With over 42 Tbps of network capacity and a global network that’s constantly learning from the over 25 million Internet properties on it, Cloudflare protects Smartx HUB against the largest and most sophisticated attacks.
- When Cloudflare’s edge data centers receive a request, they scan it to see if the visitor appears to be a threat, using criteria such as HTTP headers, user agent, query string, path, host, HTTP method, HTTP version, TLS cipher version, and request rate. We also look at HTTP response metrics such as error codes returned by customers’ origin servers.
- Our global and local DoS mitigation systems work in concert to protect new and existing threats of any size or kind against your website.
- Any resources that are already cached are served from Cloudflare’s data centers directly. Other client request traffic is sent to your origin server over Cloudflare’s high-performance network.